In such a situation, data leakage has become a sword hanging over the heads of many companies, especially for those companies that rely on core technologies. The blow caused by an internal leak is very likely to be devastating. When the technical backbone resigned, they took away all the drawings, causing counterfeit and low-priced products to quickly appear on the market. This is a real precedent that is forcing managers to re-examine the fundamental issue of data security.
Data security is the lifeline of the enterprise
In 2026, the degree of digitization is quite high, and the core assets of enterprises have long been transformed from factory buildings and equipment into digital files such as design drawings, customer data, and source codes. Once these data are leaked from the MBTI occupational test , competitors may launch homogeneous products in a very short period of time, causing R&D investment to be lost. Many small and medium-sized business owners still take chances and think that data management can only rely on trust. This actually puts the company at huge risk exposure.
Data security is not just the responsibility of technical departments; it is a strategic issue faced by top management. If there is a contract or formula that is not properly protected, it may flow into the market with the help of an ordinary USB flash drive or an inadvertent email. Establishing a systematic data protection awareness and management system is a prerequisite for an enterprise to survive and develop in the current environment. It is no less important than obtaining orders and financing.

Major risks of internal leaks
Those who have access to the company's most sensitive information are technical personnel with high authority, or sales, or financial personnel. If they lack effective technical means to restrain and audit, their behavior will be difficult to monitor. Internal leaks are the biggest threat to data security. The motivations are diverse, including retaliation for leaving the company, profit transfer, MBTI career test , or simple operational negligence.
Employees often actively leak information before and after they leave the company, and they will use the last permission period to download core information in batches. In addition, in daily work, employees use personal network disks to transfer work files for convenience, or discuss sensitive business through instant messaging tools such as WeChat. These unconscious behaviors also create hidden dangers of leakage. To nip problems in the bud, we must start by standardizing internal operating procedures.
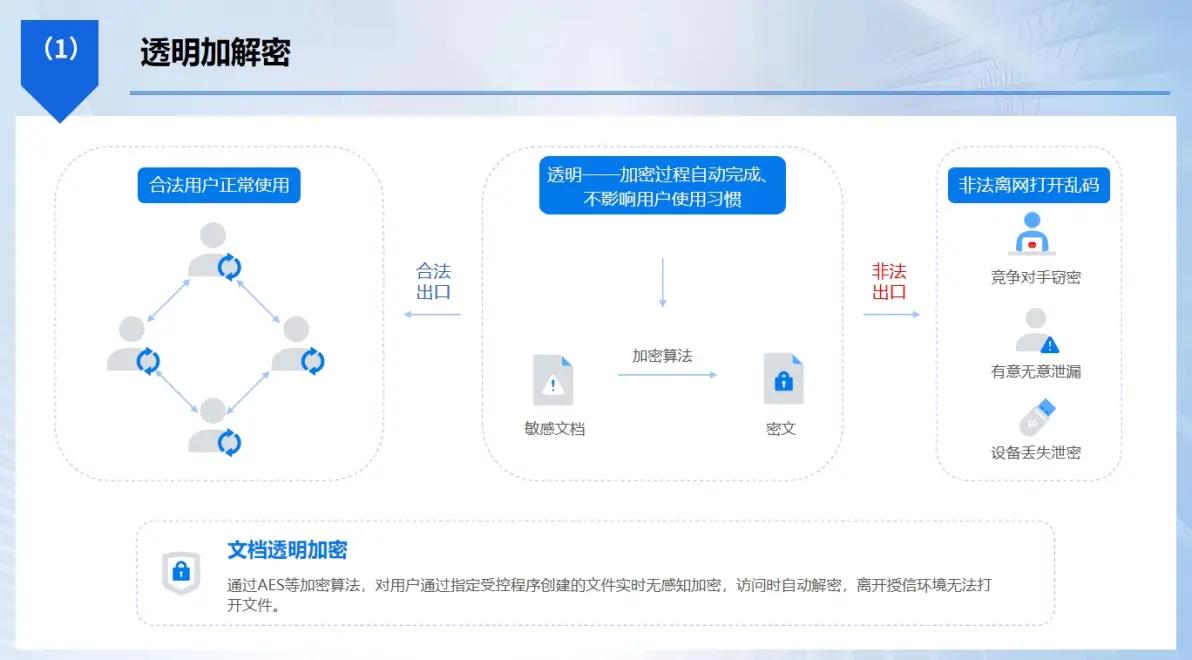
The role of transparent encryption technology
The so-called transparent encryption means that when a file is created, the file will be automatically encrypted. When the file is stored, the file will also be automatically encrypted. Employees can edit and use it normally in an authorized environment without any awareness of the whole process. When files encounter illegal attempts and are taken out of the company environment, such as when they are copied to an untrusted USB flash drive or sent over the network, they will automatically become garbled characters that cannot be opened. This technology fundamentally solves the problem of employees "forgetting" to encrypt , and also solves the problem of employees being "unwilling" to encrypt.
It uses drivers at the bottom of the operating system to achieve a mandatory encryption strategy, and implements full-process life cycle protection for specified types of files, such as CAD drawings, Office documents, etc. What this means is that no matter how the file is copied or saved, its encryption status will always follow it. For knowledge-intensive organizations such as design companies and software companies, deploying transparent encryption is the lowest-cost and most efficient way to protect intellectual property.

Behavioral auditing and advance warning
Encryption alone is not enough because there is no way to prevent employees from leaking information by taking photos or recording screens. Therefore, a system combined with employee computer behavior auditing is particularly critical. Such a system can record logs such as file operations, peripheral usage, network access, and application activities, and can conduct risk analysis based on rules. Once the system detects abnormal behavior patterns, such as massive access to core data late at night, it can immediately alert administrators.

The significance of such a function is that it has a deterrent and traceability effect. It allows employees to clearly understand that the operations they perform are within the scope of compliance supervision, thereby reducing the sense of luck. After a leak occurs, the complete operation log can provide conclusive evidence for legal accountability. Combining encryption technology with behavioral management forms a complete closed loop to prevent internal data leakage.
Tool selection for different scenarios
For those employees who often take their laptops out for activities, using full disk encryption tools such as BitLocker that comes with the operating system is a basic prerequisite. It prevents data extraction if the device is lost or stolen. For specific sensitive documents, such as individual contracts or financial statements, you can use VeraCrypt to create encrypted containers, or use AxCrypt to implement single-file encryption. The operation is simple and convenient.
R&D teams may prefer open source encryption tools that support command line and scripting, such as GnuPG, to integrate into automated processes. The AES-256 encryption function provided by the widely used compression software 7-Zip is also an effective option for temporary and secure file transfer. Enterprises should use multiple tools comprehensively based on the working patterns and data types of different departments.
Establish an overall safety culture
Even if you choose the best tool, if there is no management system and culture to match it, the effect will be greatly weakened. Enterprises must clarify the standards for data classification and stipulate the rules for access, transmission and storage of different levels of data. Employees should be regularly trained on data security awareness so that they understand the serious consequences of leaks and their personal legal responsibilities.
Management must take the lead and demonstrate compliance with security regulations, and must include data security in performance appraisals. At the same time, we use technical means to minimize the impact of security measures on work efficiency and find the key balance between security and convenience. The ultimate goal is to make data security protection a habitual work behavior and subconscious action of every employee, thereby building the most solid and stable defense system for the enterprise.

In an era where competitiveness is determined by data, has your company carried out classification work for core data, and has it equipped with corresponding technical and management protection measures? Feel free to share your own thoughts or experiences in the comment area. If you feel that this article can inspire others, please like it and share it with more people in need.



