To ensure the security of the computer, the operating system must tightly guard the door of driver loading. Microsoft's long-term driver mandatory signature policy is such a rigorous "gatekeeper". It has pros and cons and deeply affects every user.
The security value of driver signatures
Driver signature is a key protection for system security. It requires all drivers running at the kernel level to be digitally signed by Microsoft. This mechanism ensures that the source of the driver is reliable and has not been maliciously tampered with after release.
From a practical perspective, this can actually effectively block a large number of low-level malware. For example, some malicious drivers that are specifically designed to steal passwords or monitor keylogging behavior. Since they cannot obtain legal signatures, they cannot be installed on the user's computer under the default settings.
Evolution and Enforcement of Mechanisms
Driver signing was not so strict from the beginning. Microsoft introduced the relevant mechanism as early as 2006. However, administrators can still decide whether to install unsigned incentive components.
Microsoft has mandated that all kernel-mode drivers must be signed since the 64-bit version of Windows Vista appeared. This policy triggered a backlash from some developers and users at that time, but Microsoft still stubbornly insists on it as a necessary method to improve the overall stability and security of the system.
Impact on businesses and developers
A big benefit is that for enterprise IT management, the mandatory signature mechanism simplifies operation and maintenance and reduces the risk of system crashes or security incidents caused by installing drivers from unknown sources. Then enterprises can deploy standardized system images with greater confidence.
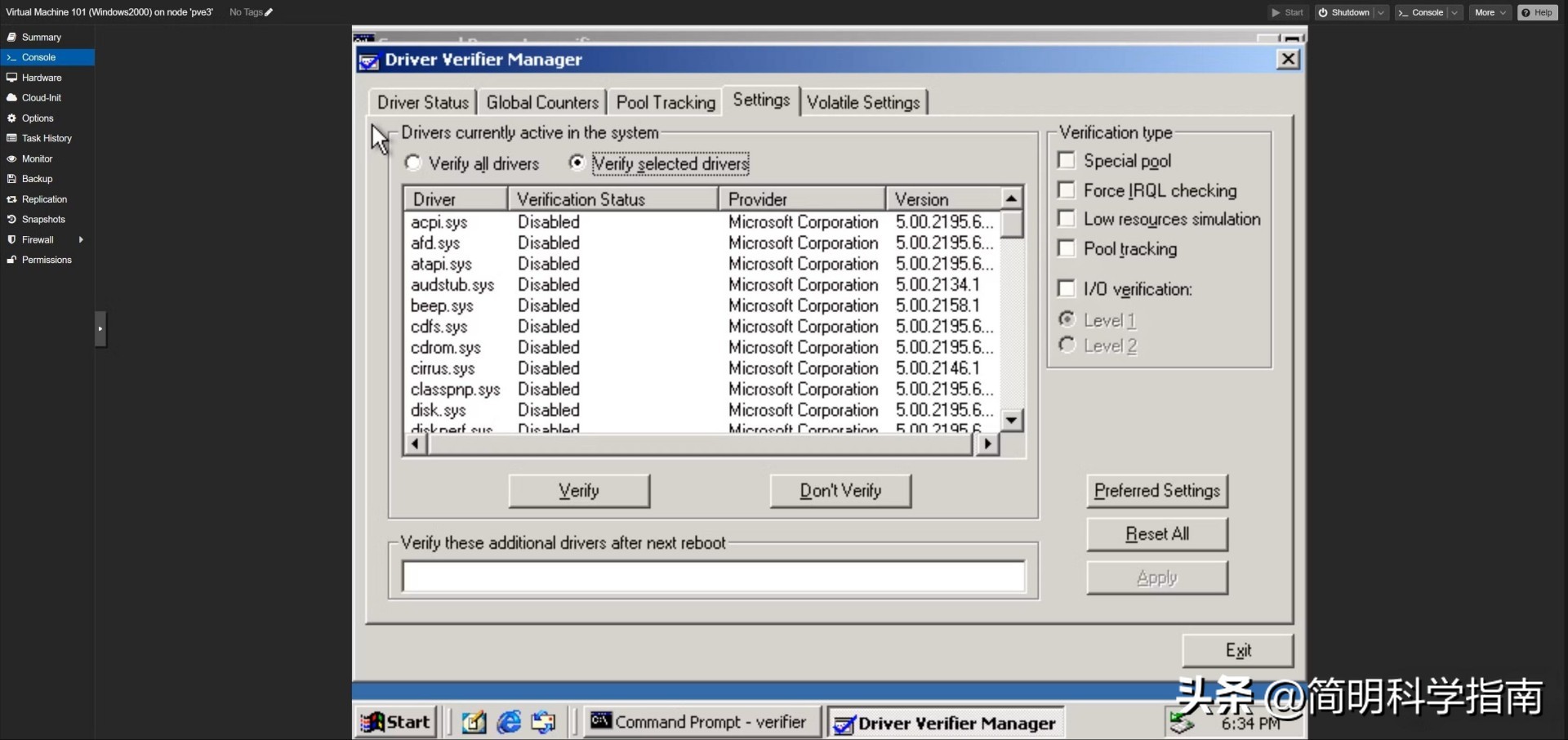
However, for those engaged in hardware development and smaller software companies, obtaining Microsoft's signature means facing extra processes and costs. They have to submit the driver to Microsoft for testing and certification, which is likely to lengthen the product development and update cycle.
Avoidance methods and potential risks
Even if mandatory signatures exist, attackers have not given up. An attack method called "driver with self-contained vulnerability" is becoming increasingly popular. Attackers will look for legitimate drivers that have successfully obtained signatures but have known security vulnerabilities.
They first induced the system to load this vulnerable but legitimate driver, and then used the driver's flaws to execute malicious code in the kernel. This method bypassed the signature check and highlighted that relying solely on the signature mechanism cannot prevent all advanced threats.
Comparison with open source systems
For open source operating systems such as Linux, no organization is as centralized and mandatory as Microsoft to sign all kernel modules. Users have extremely high autonomy and can compile modules by themselves and load modules by themselves.
This difference in freedom directly affects the construction of the security model. Linux mostly relies on code review by the open source community, timely security updates, and refined user rights management, rather than relying on a single mandatory signature to ensure security.
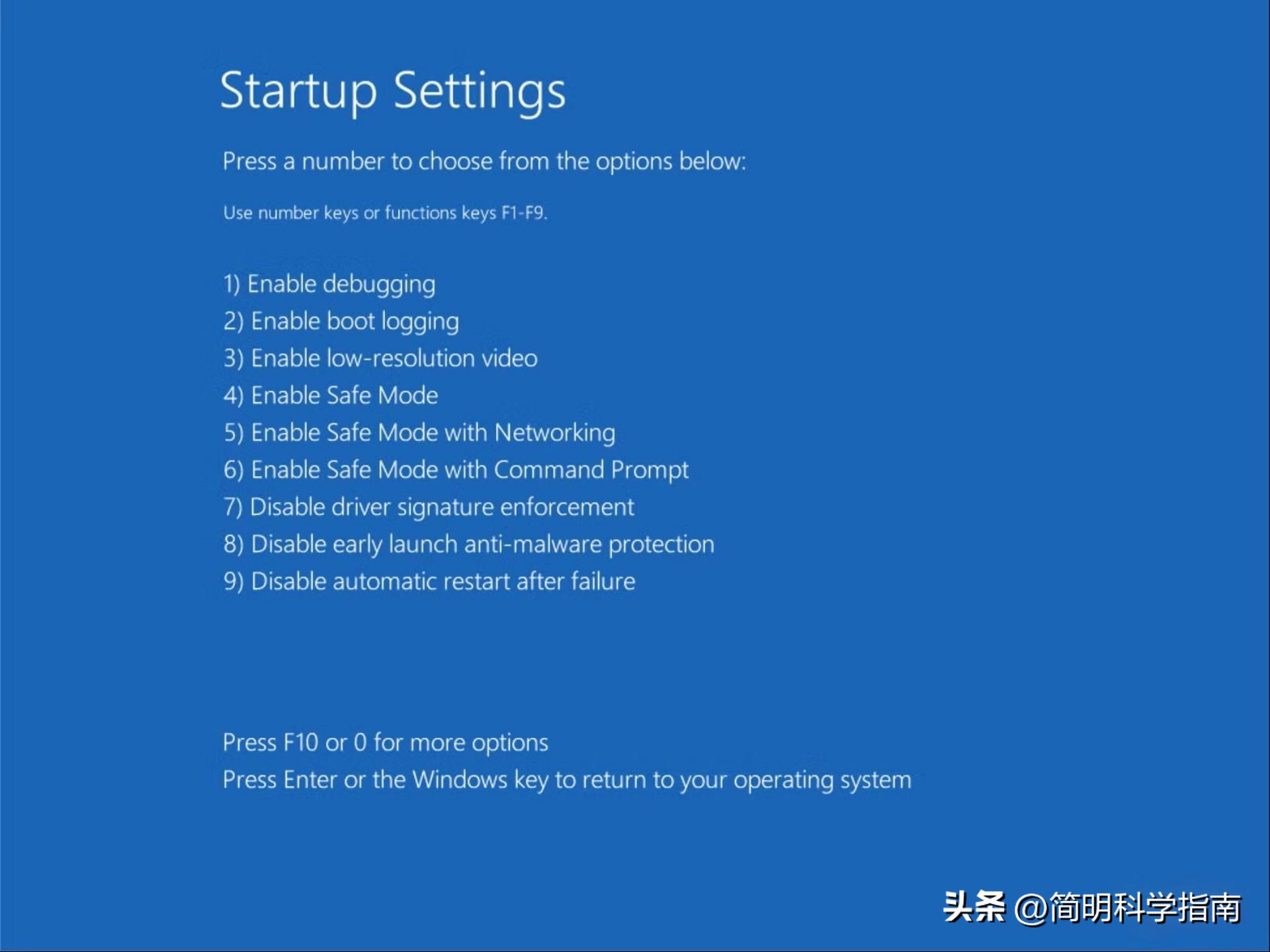
Transfer of User Control
From an essential level, driver mandatory signature represents that users give some underlying control to Microsoft. By default, the system does not trust unsigned drivers installed by users themselves, even if the user clearly knows the source and purpose of the driver.
This design concept treats ordinary users as potential risks and uses technical methods to limit the "harmful" behaviors they may do. It improves the safety bottom line of the mass market, but also abandons a certain degree of flexibility and personalized needs.
If Microsoft extends mandatory verification logic like this to more system customization areas in the future, will users' choices be further tightened? How do you view the balance between security and freedom of control?