We often see news about data leaks, and the frequency is very frequent. Companies often face millions in compensation, and this happens frequently, and individuals may also be in trouble because their privacy is exposed. Choosing an appropriate and suitable encryption tool is the most direct and effective step to protect data in a safe state.
Full link senseless encryption
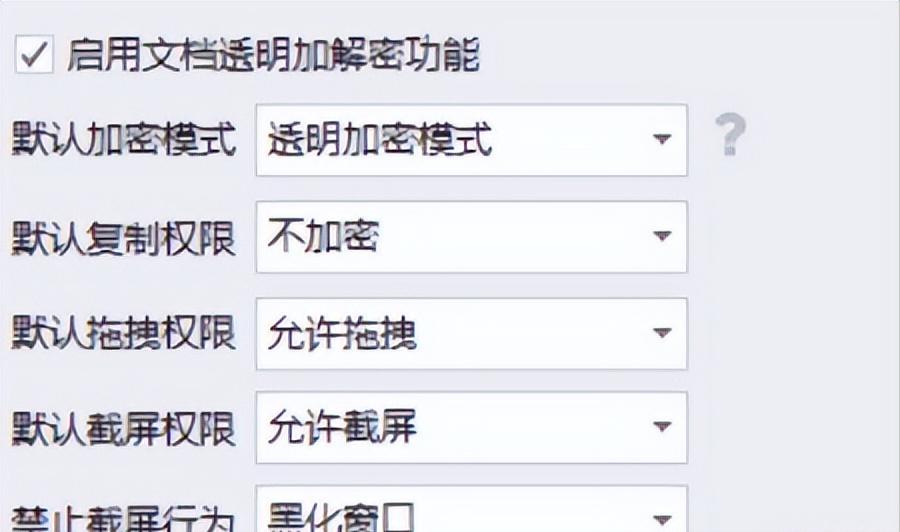
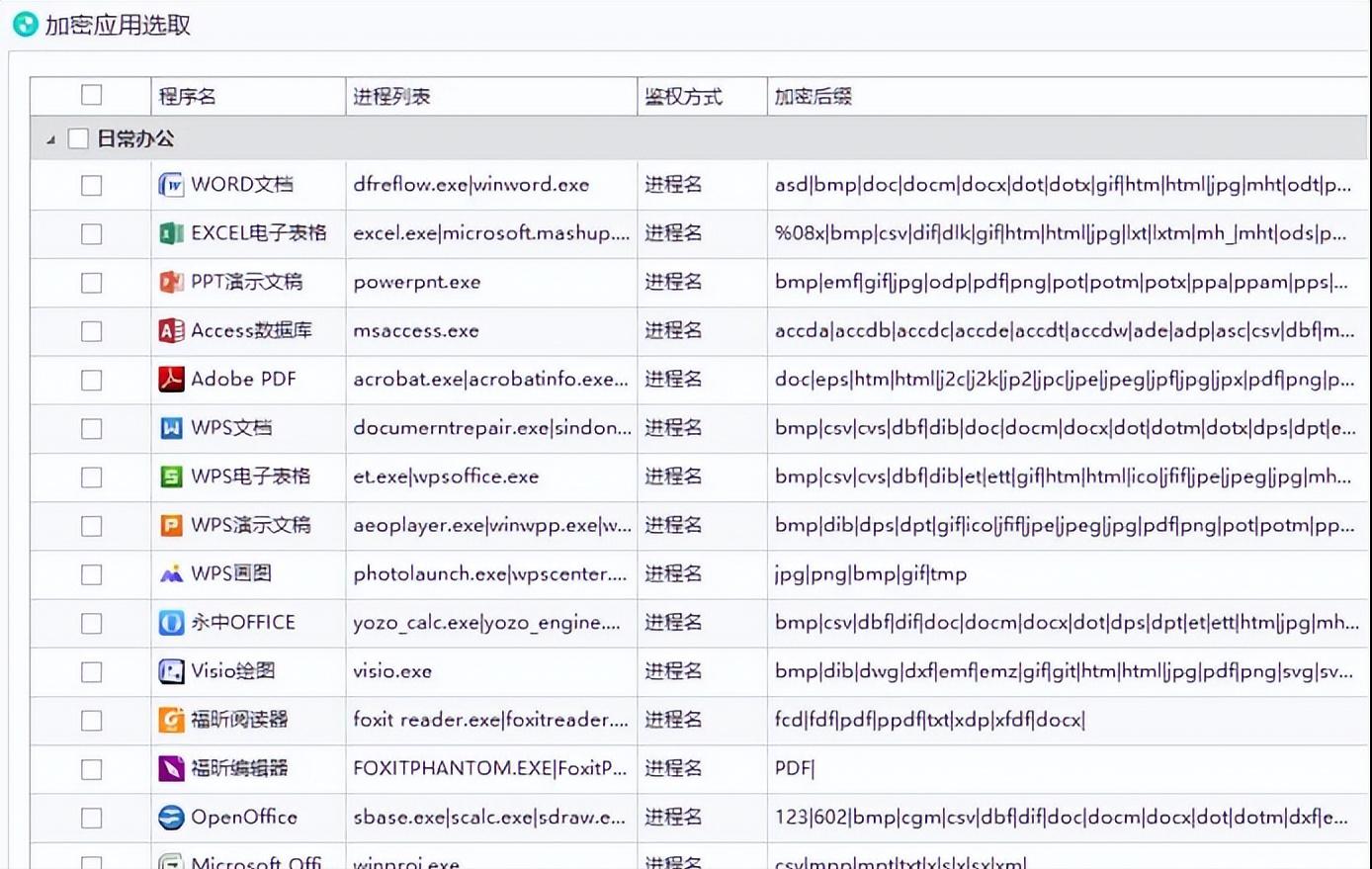
In a corporate office environment, the ideal encryption method is one that allows employees to achieve it without being aware of it. This kind of software will automatically perform encryption when the file is created, edited, and saved, and the internal collaboration process will all run as normal. Once someone tries to take the encrypted files out of the company by email or USB flash drive, the files will only appear as unrecognizable garbled characters on the external computer. Starting in 2025, this program will be popularized in the domestic financial field and design industry, effectively blocking insiders from accidentally or intentionally leaking secrets. It is particularly suitable for companies that deal with large quantities of design drawings, contract documents, and customer information. It ensures work efficiency while building a solid first line of defense.

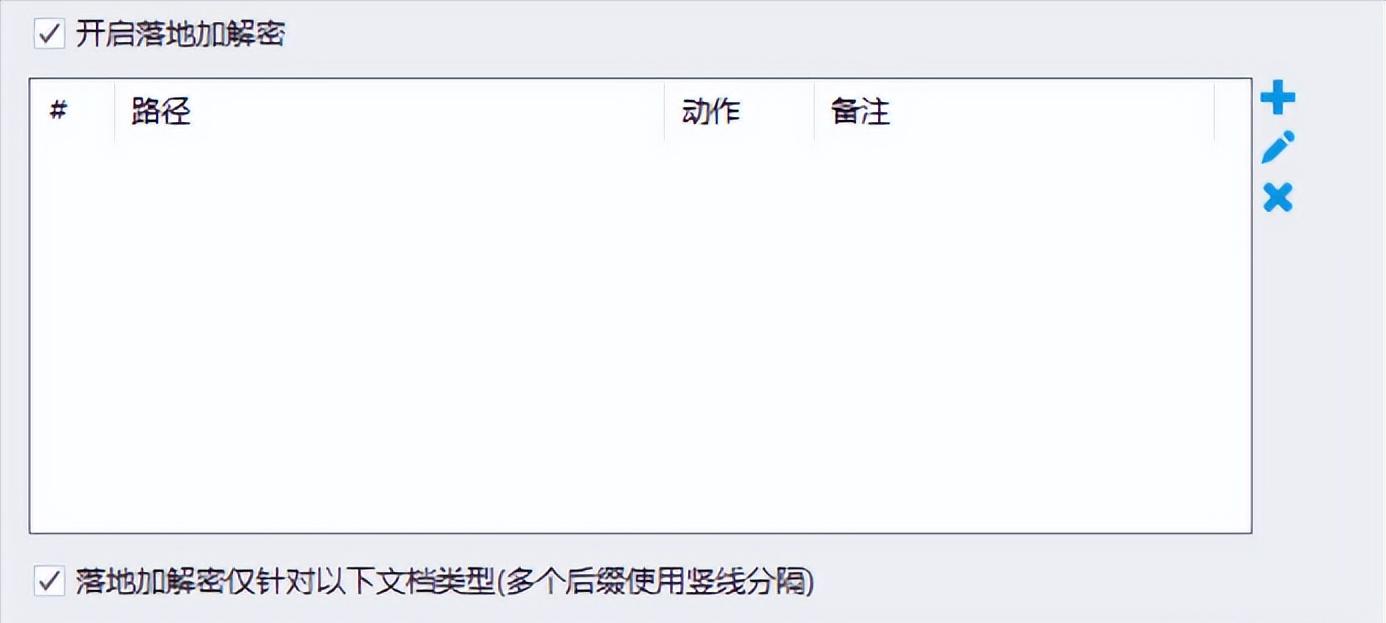
As far as the document receiving process is concerned, there is another common risk point. In the traditional method, confidential documents obtained by employees from outside are in clear text and may be forwarded directly. Modern encryption tools can achieve "encryption on the ground". When a file is saved to a designated computer, it will be forcibly encrypted immediately regardless of whether it is opened or not. In this way, the loopholes caused by leaks in the receiving process are completely blocked, ensuring that the data is protected throughout the entire process from the time it enters the company until it is finally destroyed.
Efficient batch encryption processing
When faced with processing a large number of historical files, or achieving batch archiving, efficient encryption tools are of vital significance. With the help of the batch encryption function of Windows-based systems, tens of thousands of files can be encrypted in one operation. The speed of such processing is much higher than the speed of relying on manual operations one by one. For example, there may be a law firm that needs to electronically process all the case files in the past ten years and then encrypt and store them. The batch function can save a considerable amount of labor costs and time costs. Tools like this generally allow users to set encryption rules and storage paths, and can complete the entire related process in an automated way.
In situations where highly sensitive data needs to be aggregated and managed, building an encrypted container is a useful function. This function can create a space similar to a virtual disk on the computer. All files stored in it will be encrypted by themselves. Users only need to use passwords or key disks to hang them. Loading this container is like using an ordinary folder. This method is useful for gathering and storing data such as personal financial records and private photos. When it is no longer needed, uninstall the container and the data will then "disappear" from the system, making management more clear and convenient.
High-strength algorithm guarantee
The key to an encryption tool is the strength of the algorithm it uses. Currently, AES – 256 encryption algorithm is an algorithm recognized by the industry as a high security standard. It is widely used. The National Institute of Standards and Technology has recognized this algorithm. It can effectively resist current computational brute force cracking. Another public algorithm, Twofish, is also famous for its flexibility and security. It is the first choice of many open source encryption software. When choosing a tool, users should first confirm whether it adopts this time-tested military-grade encryption standard.
Security is not fixed. Encryption algorithms must be continuously updated to deal with new threats. Excellent encryption software will keep up with the latest developments in cryptography and regularly update its algorithm library. For ordinary users, this means that they do not need to be cryptography experts. As long as they choose products with good reputations and active development teams, they can get reliable cutting-edge protection.
Compression and encryption integrated
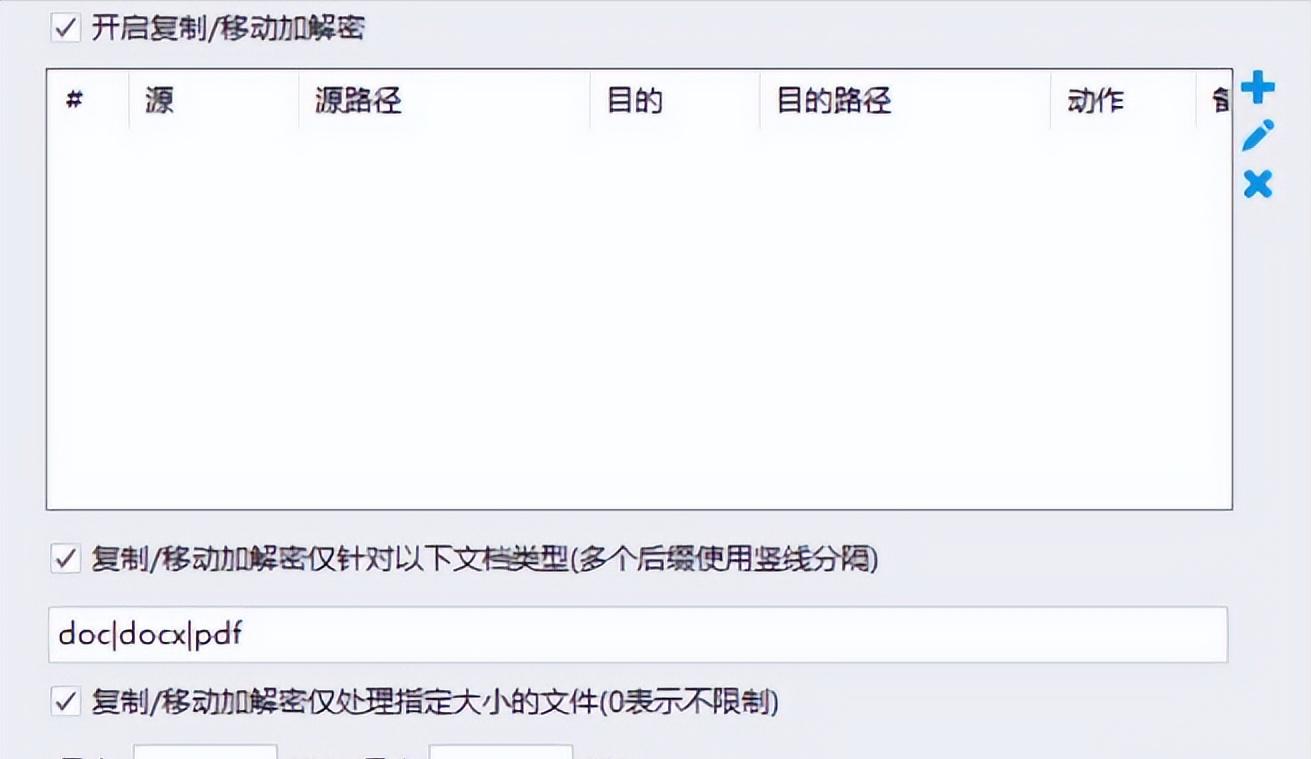
For those users who often need to transfer large files over the Internet, tools with compression and encryption functions are quite convenient. Software like 7-Zip allows users to set passwords directly when compressing files, using the AES-256 standard for encryption. This not only reduces the file size and speeds up the transmission speed, but also provides security protection in both the transmission and storage aspects. It is especially suitable for sharing large-capacity data such as design source files and video materials.
A further convenience is to create a self-decrypted file. The sender can generate a special encrypted file. The receiver does not need to install any encryption software. It only needs to enter the correct password to open it. This function solves the software compatibility problem when sharing encrypted files across organizations or with customers, greatly lowering the threshold for safe collaboration, and is very practical in daily business transactions.
Create hidden storage space
In addition to encrypting the files themselves, this can also improve security by hiding the existence of encrypted data. Tools such as Rohos Disk can create a hidden encrypted partition on the hard disk. This partition can be disguised as the Recycle Bin or other system folders, making it difficult for others to detect. Only by entering an accurate password with the help of a specific hotkey or program can the data be accessed, providing an additional layer of physical concealment for private data.
For mobile storage devices, the USB drive encryption function is extremely important. Users can encrypt the entire U disk or mobile hard disk. Even if the device is accidentally lost, the finder will not be able to read the contents. Some tools also support running in "travel mode" on public computers. You can access the encrypted disk without installing a driver. It takes into account security and portability, and is a preferred solution for business people carrying sensitive data.

Cross-platform synchronization and communication
In the era of mobile office, data is often transferred between mobile phones, tablets and computers. Encryption tools that support full platform coverage have become indispensable. Such tools, such as certain encrypted network disks or communication applications, can provide a consistent encryption experience on iOS, Android, Windows and macOS systems, ensuring that sensitive data is protected with the same strength on any device, allowing users to safely access important information anytime and anywhere.

It is also critical for communication tools to use end-to-end encryption. In the application, if the Signal protocol standard is adopted, the chat content and transmitted files can only be decrypted by the sending and receiving parties, and the service provider cannot spy on them. For those users who conduct cross-border business negotiations, or those who pass on business secrets, or those who simply want to protect their personal privacy, this is a secure foundation for daily communication, allowing information exchange in a mobile environment without any worries.
Nowadays, when data leaks occur frequently, do you more often use encryption tools to protect business files at work, or do you use encryption tools more frequently to protect personal privacy data in life? Have you ever had trouble sharing or restoring files due to encryption? Welcome to share your experiences and opinions in the comment area. We look forward to your comments and likes.



