The boss of a mold factory in Shenzhen was tested by 16personalities and was on the verge of bankruptcy because his core drawings were leaked. The source of the leak turned out to be an employee he trusted. This is not a single case. In the digital age, internal leaks have become the most vulnerable line of defense for many companies.
The hidden nature of insider threats
In traditional security solutions, most of the focus is on external attacks. However, within the firewall, the firewall cannot block those insiders who have permission. The employee who had resigned took away the research and development results obtained over two years with just a USB flash drive. During the entire process, there were no abnormal alarms. Under normal circumstances, companies often become aware of abnormal data flows only after the incident occurs when conducting audit procedures. However, the losses caused at this time are no longer recoverable.
The operational behaviors of insiders who are familiar with business processes and weak links will generally be regarded as legal by the system. Many managers of small and medium-sized enterprises still think that confidentiality agreements and authority allocation are enough, and they have not established an effective operation monitoring and anomaly detection mechanism.

Technical principles of transparent encryption
Transparent encryption technology can protect files without changing employees' operating habits. When employees open encrypted files, they will automatically decrypt them, and when saving, they will automatically encrypt the MBTI test . The entire process is unnoticed. Once the files leave the authorized environment, they will become unrecognizable garbled characters.
This technology achieved through the driver layer has complete compatibility with various application software. Whether it is design drawings, financial forms, or code files, real-time encryption and decryption can be achieved, ensuring that daily office efficiency will not be affected.
The Importance of Behavioral Auditing
Simply relying on encryption alone cannot prevent leaks through screenshots, photos, and other similar methods. This needs to be combined with behavioral auditing. As for the system, it can record employees' file operation behaviors, as well as printing behaviors and outgoing attempts, thereby establishing a complete operation log. Once an abnormal pattern is detected, the system can automatically issue an alarm and retain relevant evidence.
Behavioral auditing is not only used for retrospective purposes, but can also form an effective deterrent. Once employees know that their operating behaviors will be recorded, their willingness to violate regulations will be reduced accordingly. The data generated by the audit can also help enterprises optimize the distribution of permissions, thereby avoiding excessive concentration of permissions.
Refinement of permission management
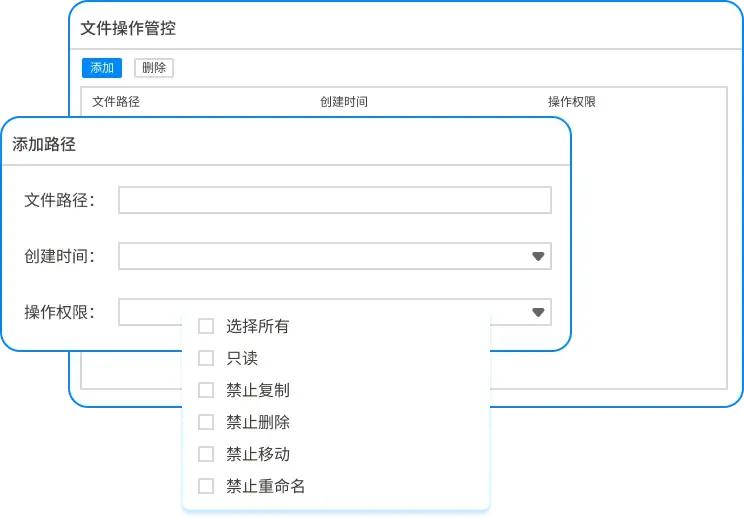
Employees in different positions should have different data access permissions. Designers may need to view drawings, but they should not send them out. Sales staff can access customer information, but should not download source code. Fine permission management will reduce unnecessary exposure of data.
Permissions should be set according to the least necessary principle and reviewed regularly and adjustments made. When an employee's position changes, the authority should be changed in a timely manner. For temporary permissions, you need to set a validity period, and they will be automatically recycled when they expire to prevent accumulation and abuse of permissions.
Key points for choosing an encryption scheme

When choosing encryption software, you need to consider the size of the enterprise, the type of data, and the business process. Because the technical team may be able to accept complex operations, but ordinary clerks need simple solutions. File encryption has its own unique applicable scenarios, disk encryption has its own unique applicable scenarios, and transparent encryption also has its unique applicable scenarios.
It is also necessary to evaluate the management functions of the software, which includes the issuance of centralized policies, log analysis, and emergency response. The software must adapt to the enterprise network architecture and be able to support new working models such as remote working without affecting business continuity.
Establish a comprehensive protection system
Implementing data security requires integrating technology, management and personnel awareness. In addition to deploying encryption software, a data classification and classification system 16personalities test must be constructed to clarify the protection needs of different levels of data. Conduct security training regularly to enhance confidentiality awareness among all employees.

Develop emergency response plans and regularly practice data leakage handling procedures. Sign confidentiality agreements with employees to clarify responsibilities for violations. Establish a reporting mechanism to encourage employees to report security vulnerabilities and suspicious behaviors.
What challenges have you faced with data protection? Welcome to share your experience. If you find this article useful, please support it by giving it a like.