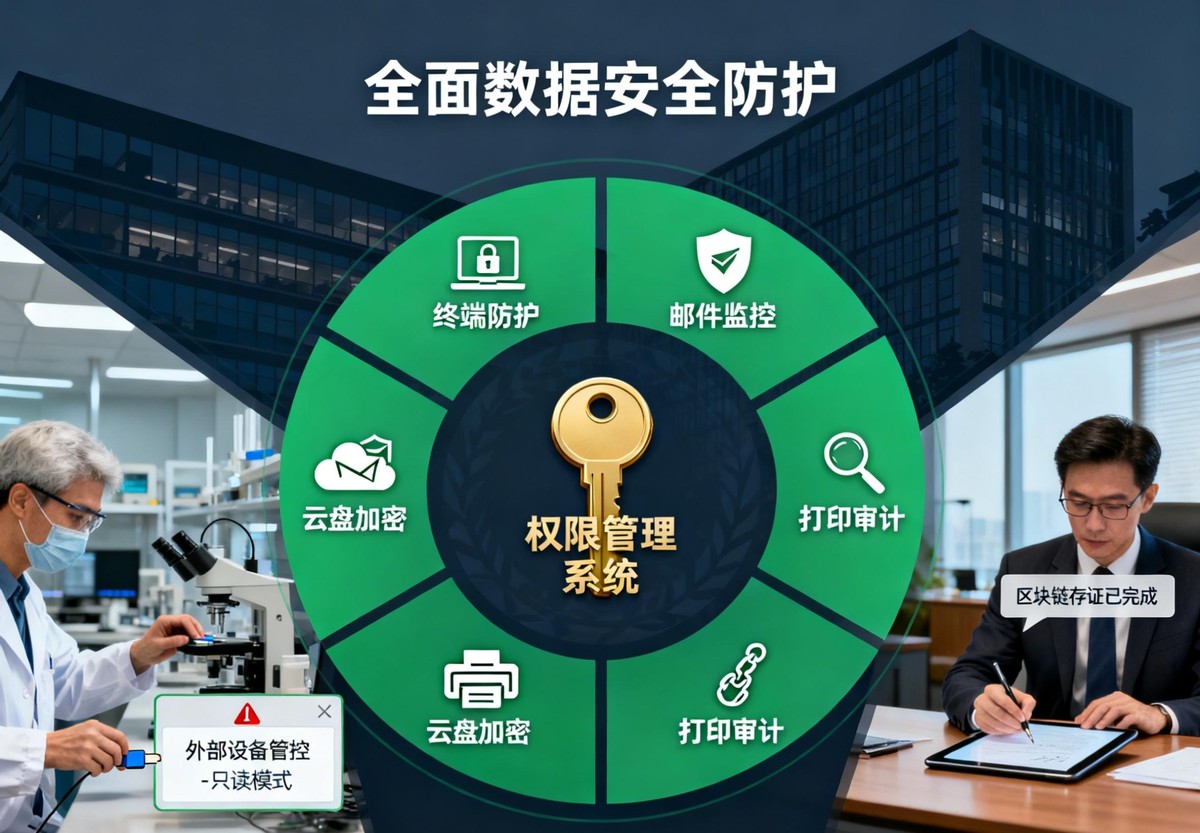
Drawings and codes are the core assets of an enterprise, but security issues are always present. If employees misoperate, take them away when they leave, or have them stolen by outsiders, they may cause heavy losses. Faced with encryption software with different functions on the market, how to choose a solution that truly suits them has become a problem faced by many managers and technical teams.
How to define your security needs

The first step is to choose encryption software by clearly identifying what you want to protect. You have to distinguish whether the MBTI career test protects static data stored on servers or computer hard drives, or data with dynamic characteristics during use and circulation. Static data protection emphasizes preventing reading when a device is lost or abandoned, while dynamic data protection requires controlling who can perform what operations on files at what time.
Because different industries have different needs, and this difference is really huge, the core of software companies is considered to be source code, architectural design institutes worry about CAD drawings, while law firms focus on contracts and evidence documents. Clarifying their most sensitive data types and their usage scenarios is the basis for avoiding waste of investment and achieving accurate protection. Blindly pursuing a comprehensive MBTI personality test often makes deployment complicated and inconvenient to use.
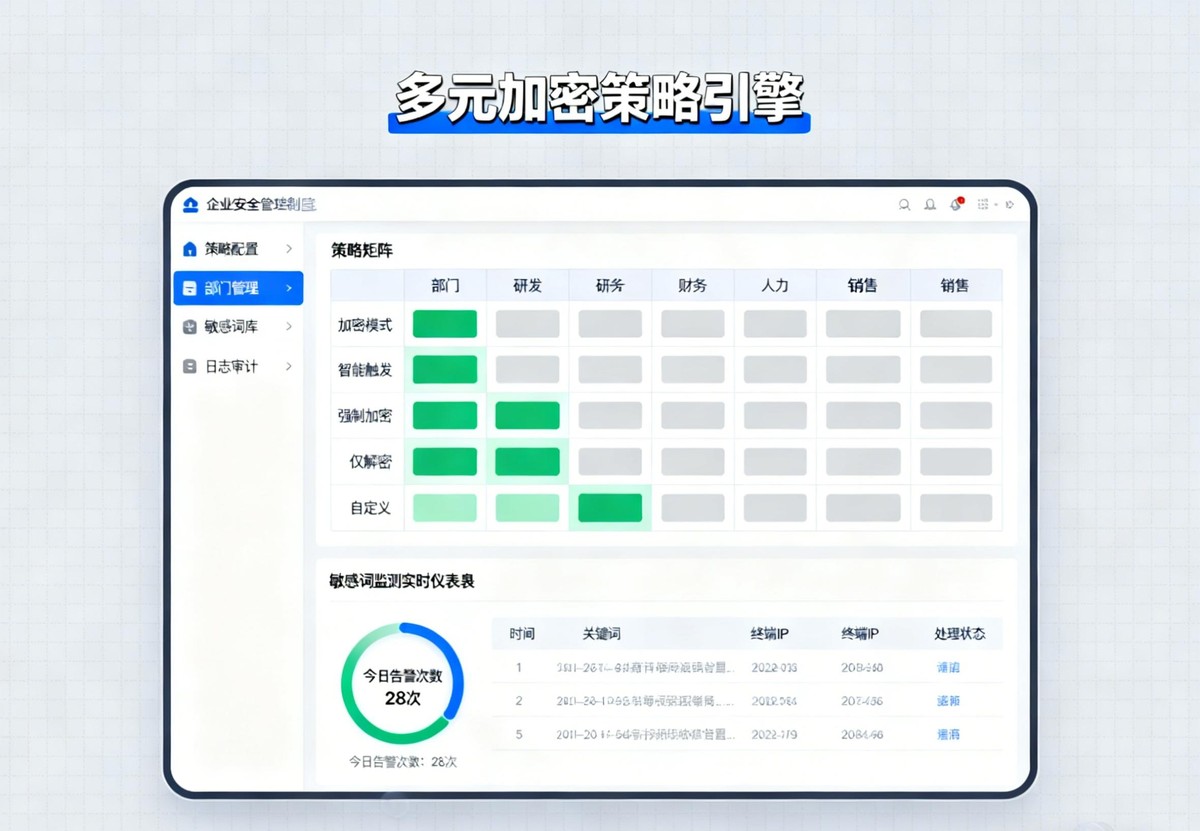
Enterprise-level full life cycle protection
For companies engaged in R&D and high-end manufacturing, data security covers the entire process from creation to destruction. Such solutions generally work at the bottom of the operating system and automatically encrypt specified file types such as .java and .dwg. Employees who are legally authorized will not notice when opening files in a controlled environment. However, in the event of unauthorized copying or outsourcing, the file cannot be opened.

This type of platform will provide sophisticated permission management, and can set up security zones based on departments or projects, and control whether files can be printed, screenshotted or edited. All operations will be recorded in detail. They can also use invisible dot matrix watermarks to achieve precise traceability after leaks. At the same time, they provide secure file outgoing functions and can limit the number of times external partners can open files and their validity period.
Cornerstone protection built into the operating system
For the majority of companies using Windows systems, BitLocker provides a basic and important protection method. It uses the method of encrypting the entire hard drive to prevent data leakage in the event that the computer or hard drive is physically lost or stolen. It is deeply integrated into the system and can work together with the Trusted Platform Module (TPM) chip to provide hardware-level secure boot verification.

BitLocker is more convenient to deploy. Administrators can use domain policies to carry out centralized management and policy distribution. It is suitable for meeting the basic terms of "storage media encryption" in compliance requirements and is the cornerstone of the data security defense line . However, it does not involve file-level permission control and operation auditing. It mainly solves static data security issues at the device level.
Lightweight and flexible daily file protection
Often some individual users or small teams have the need to quickly encrypt certain sensitive documents, such as scans of personal ID cards, undisclosed plans, and design drafts. At this time, some lightweight tools will be more appropriate. They generally have simple interfaces, and can quickly encrypt and decrypt using the right-click menu. They can also disguise encrypted files as ordinary pictures, which has a certain degree of concealment.
Often these tools support national encryption algorithms and can be used in conjunction with network disks to achieve secure synchronization such as "local encryption and ciphertext storage in the cloud." They eliminate the risk of leakage when transmitting sensitive files via social media or email. They are also suitable for simple and secure data sharing within freelancers and small and micro teams, balancing security with operational convenience.

Exclusive solution for mobile storage devices
In terms of personnel, for those who often need to carry data on business trips or work between different computers, the data security of USB flash drives and mobile hard drives is extremely critical. There is a portable encrypted container software that is specially designed for this scenario. It can create an encrypted virtual drive letter on a USB flash drive that requires a password before it can be opened, achieving the goal of "portable data, safe and secure".
Its advantage is reflected in "plug and play". After installing the client on a commonly used computer, you can enter the password on any other computer to access the encrypted area without having to install software on other people's computers. This method is particularly suitable for sales staff to carry customer information, for programmers to transfer project codes, and for designers to carry out mobile offices, ensuring that data will not be leaked when the mobile media is lost or a computer is borrowed.
Special protection for programming languages

For software development companies, especially those using specific languages such as Ruby, source code is core intellectual property. General encryption software may be incompatible or affect code operation, so language-specific protection tools are needed. Such tools can obfuscate source code, such as renaming variables, and perform selective encryption, making the code difficult to decompile and tamper with after it is delivered to customers.
It can deeply understand language features, prevent running errors in protected code, and can be integrated into the continuous integration/delivery (CI/CD) process. This is especially suitable for companies that distribute Ruby Gem as a commercial product, or that need to protect the core business logic code of the SaaS platform. When distributed as a closed source, it ensures that the code can run normally.
After comparing different types of data security solutions, do you think that for a software startup company with about 50 people, which level of protection should be deployed first and is the most important when costs are limited? Welcome to share your views in the comment area.