In recent years, certain social software that uses the banner of "encryption" as a selling point has become something that criminals use to conceal themselves when committing crimes, like clothing, and has also unknowingly penetrated into the mobile phones used by some teenagers.
Encryption software becomes a criminal tool

This type of software is often used frequently in telecommunications network fraud, online gambling, pornography and other illegal and criminal activities. Criminals use its point-to-point encryption and "burn after reading" functions to destroy communication evidence, which poses a huge challenge to the police's tracing and evidence collection. They were created for user privacy, but in reality they provide shelter for dark transactions, and their technical features are being severely abused.
The physical location of servers has been set up overseas to further circumvent supervision. This causes law enforcement agencies to face complex processes and higher costs in cross-border collaboration and technical cracking even if they find clues. "Technical shield" objectively reduces the risk of crime and attracts more criminals to gather, thus forming a new ecology of online crime.
Technological upgrades make detection more difficult
The criminal tools that have transformed from the pseudo base stations of the past have advanced into professional devices such as GOIP and Doka. These devices have the ability to remotely control multiple mobile phone numbers to make calls or send and receive messages, thereby achieving a state of human-machine separation and remote operation. It is very likely that fraudsters living abroad can use the Internet to control domestic equipment and fake local numbers to commit fraud. Their concealment characteristics are extremely prominent.
The space for criminals to commit crimes has extended from traditional telecommunications networks to new areas such as virtual currencies and third-party payments. Funds flow very quickly and are difficult to track. Illegally obtained money is often migrated and cleaned in a short period of time through multi-layered accounts. This puts unprecedented requirements on the public security organs' emergency stop payment and fund flow investigation and control capabilities.
Student groups become key targets
Due to their lack of social experience and strong curiosity, teenagers can easily become the primary target of online fraud. Criminals often engage in chatting behavior in game communities and short video platforms, using "free skins" and "red envelope rebates" as bait. Once the children's trust is gained, they will be guided to leave the original platform and go to encrypted software for in-depth communication, thereby avoiding the supervision of parents and conventional software.
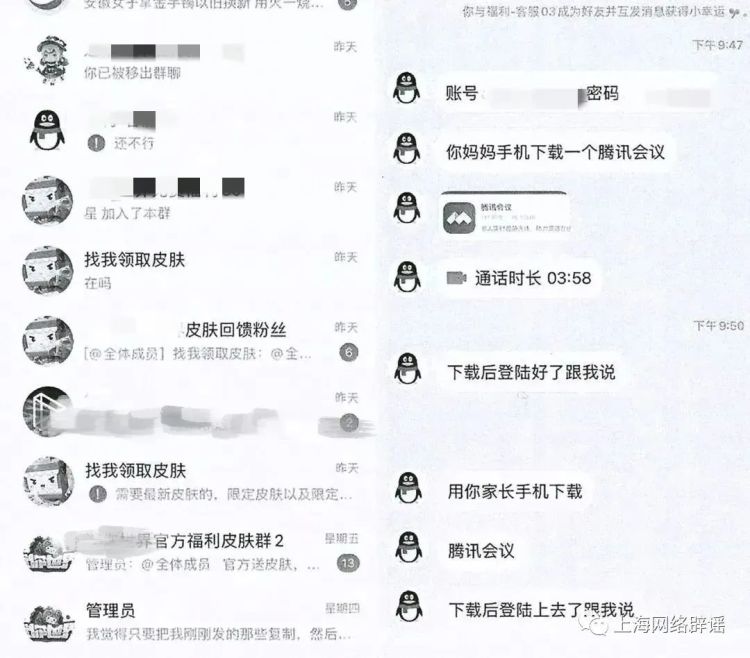
In the private chat environment created by encryption software, scammers use emotional coaxing, promises of benefits, or intimidation and threats to induce minors to give out personal information, mobile phone verification codes, and even deceive parents into paying passwords. Without knowing it, some children use their identity information to apply for phone cards or bank cards for criminals, and then become "tools".
Be wary of the trap of “criminal assistance”
The crime of assisting information network crimes, in short, is knowing that others are using the Internet to commit crimes, but still providing technical support or assistance. In actual situations, many teenagers do not have a clear concept of this. They may rent their real-name authenticated bank cards and payment accounts to others just for a few hundred yuan in benefits, and these accounts are quickly used to receive fraudulent funds.
If the turnover involved in the case reaches a certain amount, even if the person who provides the account claims that he has no knowledge, he may be held criminally responsible for the crime of "helping and trusting". This will not only leave a criminal record, have an impact on further education and employment, and may also face fines. Parents must clearly inform their children that renting or lending personal accounts and identity information is definitely not a trivial matter.
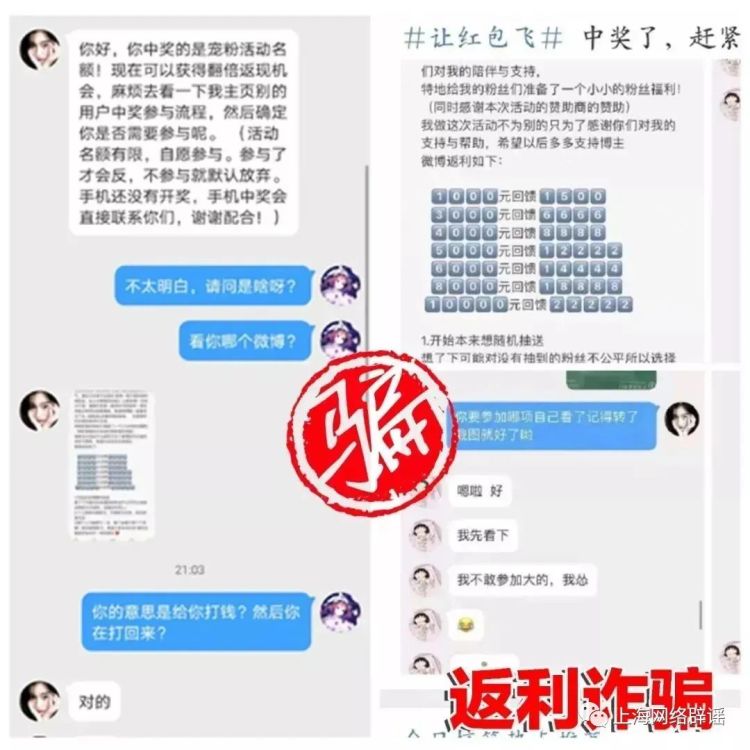
Common student scams
For underage players, disabling the "anti-addiction system" is a common scam in recent times. Scammers say there are channels to lift restrictions on game time, and also require children to use their parents' mobile phones to operate through screen sharing or sending specific instructions. During this operation, the payment password and verification code are particularly easy to be stolen, causing the funds in the account to be stolen.
Another scheme is the so-called "celebrity fan welfare" fraud. A group of scammers will pretend to be celebrities or their assistants, build fake fan groups on social platforms, and request transfers through pretexts such as recharging support, paying group membership fees, or receiving signed photos. They rely on children's admiration to create a sense of urgency, causing children to rush into operations before they have time to verify.
Protective measures parents should take

Parents should check their children's mobile phones regularly. Not only should they check the application list, but they should also pay attention to whether there is software that hides icons or uses icons such as calculators and alarm clocks to disguise their behavior. If you come across software that is not necessary for children and that children do not understand, especially software that promotes so-called "encrypted chat", you must uninstall it immediately. In addition, payment permissions for electronic devices used jointly by the family must be properly managed.
During daily education, be sure to clearly inform your children that any behavior that requires passwords, verification codes, screen sharing, or private transfers is a scam. Parents should set the payment account to a strong password that is independent and unknown to the child, and turn off the small-amount password-free payment function. To make an agreement with your children, any operation involving money must first be confirmed with the parents in person.
In the current situation where technology continues to provide new cover for crime, should we think again about how to achieve a balance between stimulating technological innovation and protecting social security? You are welcome to share your views in the comment area. If you think this article is useful as a reminder, please like it to support it.