The core resource that drives the development of the digital economy is data. However, in the process of mining its value, data security and privacy issues are like an insurmountable gap that separates data supply and demand.
The market’s urgent demand for data circulation
All walks of life now expect to use data cooperation to optimize business, such as financial risk control and precision marketing. The enterprise's own data often cannot support a complete analysis model, so external data sources need to be introduced. Such demand creates the need for a trusted and compliant data transaction environment. However, direct exchange of raw data will face huge legal and commercial risks, which hinders the release of the value of data elements.
Privacy leak risks and compliance challenges
In actual operations, data circulation encounters two major problems. One is technical risk. Once the original data leaves the local area, it may be copied, abused, or leaked. The second is compliance pressure. At home and abroad, regulations such as the "Personal Information Protection Law" are becoming increasingly strict, providing clear audit and authorization requirements for data transaction processes. Companies are worried that data cooperation will hit legal red lines, so they are extremely cautious in their actions.
Core functions of data circulation platform
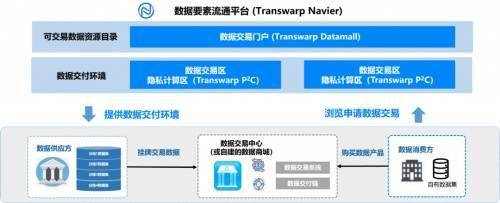
In response to these pain points, professional data circulation platforms have emerged. This type of platform regards the core role of a trusted and neutral third party to build a bridge between data providers and consumers. It helps providers safely release data catalogs and samples. It allows consumers to detect data quality and initiate cooperation requests without touching the original data. The entire transaction process is monitored and recorded by the platform.
The cornerstone role of privacy computing technology
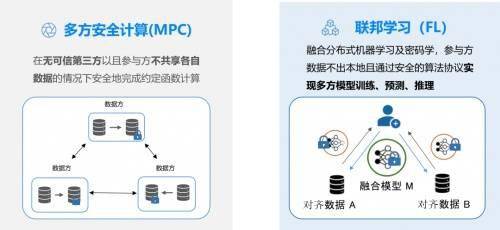
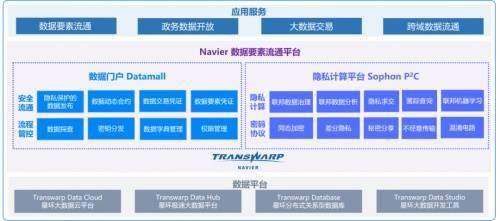
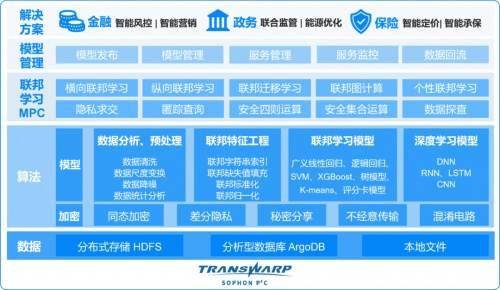
The key to achieving "data availability and invisibility" relies on privacy computing technology. Currently, the mainstream technology routes used cover multi-party secure computing, federated learning, and trusted execution environments. Multi-party secure computing uses cryptographic protocols to prompt multiple parties to perform calculations together, but their respective data will not leave the local area. Furthermore, federated learning allows the algorithm model to go to various data sources for training, while the original data remains unchanged. These technologies ensure the safety of the circulation process from a lower level.
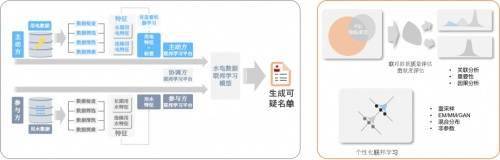
From technology platform to business solutions
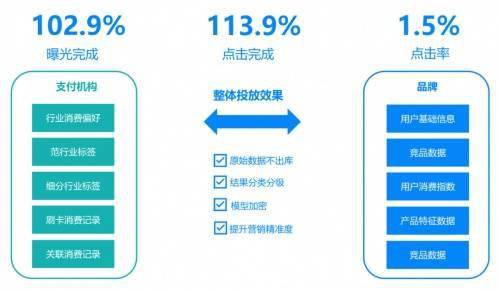
A mature platform is not just a collection of technical tools, it needs to be able to solve actual business problems. For example, in automobile marketing scenarios, the platform can help brands securely combine payment platform data and build more accurate user portraits while protecting user privacy. In this way, we can effectively identify the authenticity and value of sales leads, activate hundreds of millions of lead resources, and then transform them into actual sales opportunities.
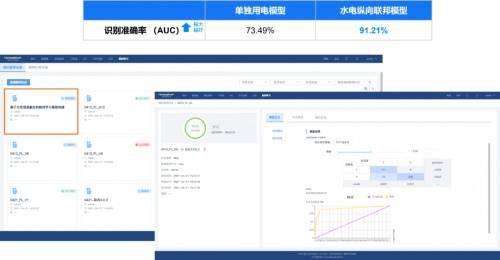
Key elements for successful platform implementation
For a platform to be truly put into use, it must have several key capabilities. Particularly critical is the full-link data privacy protection configuration solution, which must cover the entire process from collection to accounting. At the same time, the platform needs to obtain certification and recognition from authoritative organizations, such as passing relevant tests by the China Academy of Information and Communications Technology, in order to prove its safety and reliability. In addition, easy-to-use and convenient attributes and flexible deployment and configuration methods, such as whether it can support cloud or local deployment, can truly effectively lower the use threshold for enterprises and improve the convenience of use.
You may ask, in the future when data elements circulate, apart from the technology itself, will the biggest challenge be the establishment of mutual trust standards between industries, or the deeper refinement and unification of laws and regulations? You are welcome to share your opinions in the comment area, and sincerely please like this article to support it.